Generate crypto key cisco asa images are ready in this website. Generate crypto key cisco asa are a topic that is being searched for and liked by netizens today. You can Find and Download the Generate crypto key cisco asa files here. Find and Download all royalty-free images.
If you’re looking for generate crypto key cisco asa images information connected with to the generate crypto key cisco asa keyword, you have visit the ideal site. Our site always provides you with hints for seeing the highest quality video and picture content, please kindly search and find more informative video articles and images that fit your interests.
Generate Crypto Key Cisco Asa. The ecdsa algorithm is a part of the elliptic curve cryptography ecc and uses an equation of an elliptic curve to generate a public key whereas the rsa algorithm uses the product of two primes plus a smaller number to generate the public key. For these key to work you should have a hostname domain name configured on the asa as well unless you configure a dedicated rsa keys. What s new for cisco defense orchestrator cdo. Router config crypto key generate rsa label mykeys redundancy.

Choose the size of the key modulus in the range of 360 to 2048 for your. Within the trustpoint the previously created key pair is assigned and certificates dn is defined. The name for the keys will be. Ciscoasa config crypto key generate rsa label fir3net key modulus 1024 info. The link to join the discussion will be activated on january 11 this event is a chance to discuss cisco adaptive security appliance asa and firepower threat defense. Previously i have always generated a crypto key pair when configuring an asa from scratch.
Router config crypto key generate rsa label mykeys redundancy.
Ssh config and crypto key generate rsa command. Use this command to generate rsa key pairs for your cisco device such as a router. Ciscoasa config crypto key generate rsa label fir3net key modulus 1024 info. Crypto key generate rsa. The name for the keys will be. Before generating a csr request you must create a private key config crypto key generate rsa label itadminguide key modulus 2048 info.
 Source: newwell102.weebly.com
Source: newwell102.weebly.com
The following example specifies the redundancy keyword. The name for the keys will be. Crypto key generate rsa. If your router already has rsa keys when you issue this command you will be warned and prompted to replace the existing keys with new keys. Generate csr via cisco asa cli commands 1.
 Source: mustbegeek.com
Source: mustbegeek.com
Crypto key generate rsa signature. Crypto key generate rsa signature. The ecdsa algorithm is a part of the elliptic curve cryptography ecc and uses an equation of an elliptic curve to generate a public key whereas the rsa algorithm uses the product of two primes plus a smaller number to generate the public key. Crypto key generate rsa general keys label tokenkey1 storage usbtoken0. Router config crypto key generate rsa label mykeys redundancy.
 Source: youtube.com
Source: youtube.com
Keys are generated in pairs one public rsa key and one private rsa key. The asas do have vpns configured. The name for the keys will be. Choose the size of the key modulus in the range of 360 to 2048 for your. The following example specifies the redundancy keyword.

The following example specifies the redundancy keyword. Use this command to generate rsa key pairs for your cisco device such as a router. Before generating a csr request you must create a private key config crypto key generate rsa label itadminguide key modulus 2048 info. The name for the keys will be. Keys are generated in pairs one public rsa key and one private rsa key.
 Source: m.youtube.com
Source: m.youtube.com
Use this command to generate rsa key pairs for your cisco device such as a router. Crypto key generate rsa signature. The asas do have vpns configured. Mykeys choose the size of the key modulus in the range of 360 to 2048 for your general purpose keys. Generate csr via cisco asa cli commands 1.
 Source: cisco.com
Source: cisco.com
If your router already has rsa keys when you issue this command you will be warned and prompted to replace the existing keys with new keys. The name for the keys. The following example specifies the redundancy keyword. Next a trust point is created. Ciscoasa config crypto key generate rsa label fir3net key modulus 1024 info.
 Source: networkguy.de
Source: networkguy.de
Keys are generated in pairs one public rsa key and one private rsa key. Next a trust point is created. Ciscoasa config crypto key generate rsa label fir3net key modulus 1024 info. Mykeys choose the size of the key modulus in the range of 360 to 2048 for your general purpose keys. The name for the keys will be.
 Source: community.cisco.com
Source: community.cisco.com
Fir3net key keypair generation process begin. This means that with ecdsa the same level of security as rsa can be achieved but with smaller keys. Fir3net key keypair generation process begin. Crypto key generate rsa. The name for the keys will be.
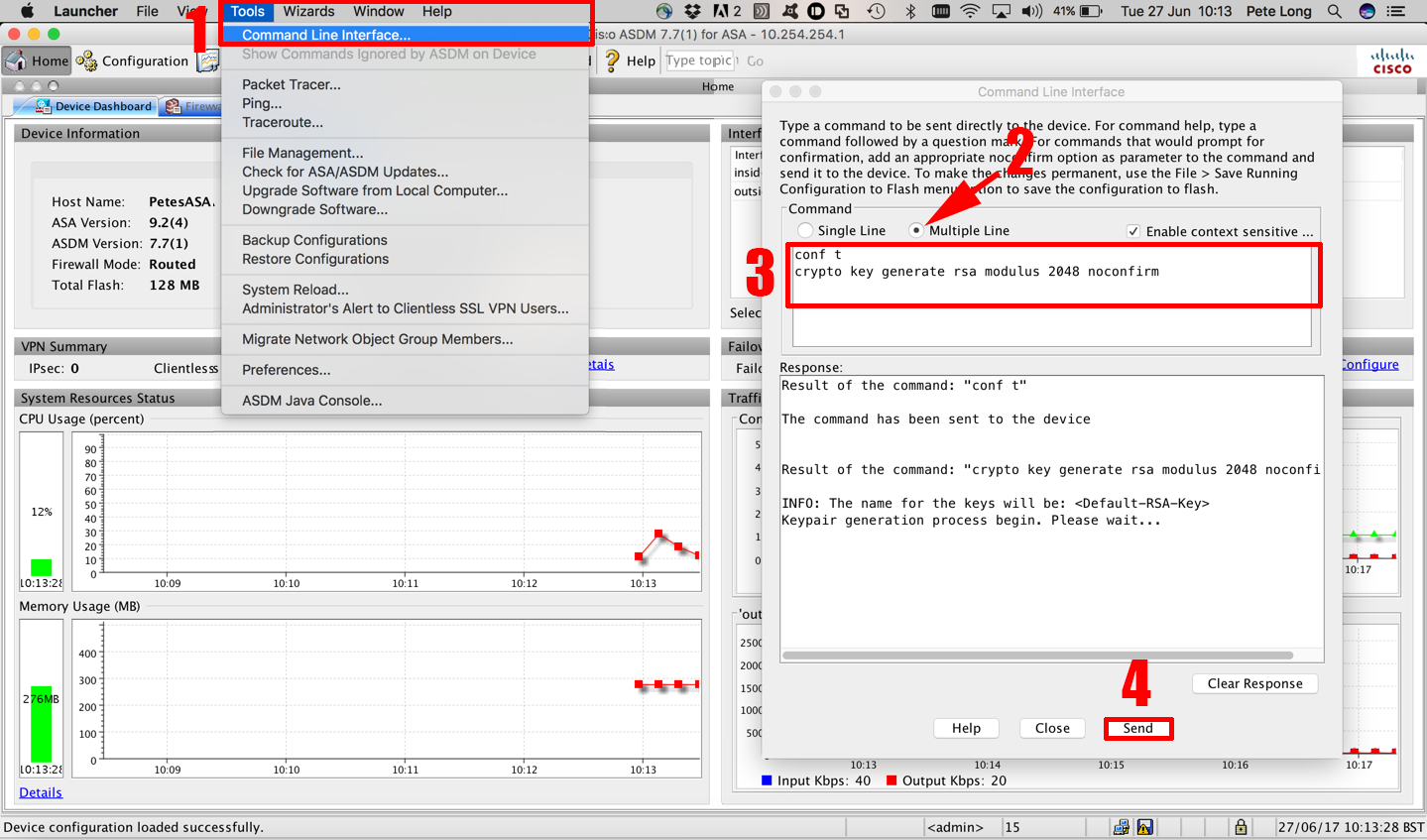 Source: petenetlive.com
Source: petenetlive.com
So basically configure a hostname domain name and generate the rsa key pair. Fir3net key keypair generation process begin. Keys are generated in pairs one public rsa key and one private rsa key. Generate csr via cisco asa cli commands 1. Crypto key generate rsa general keys label tokenkey1 storage usbtoken0.
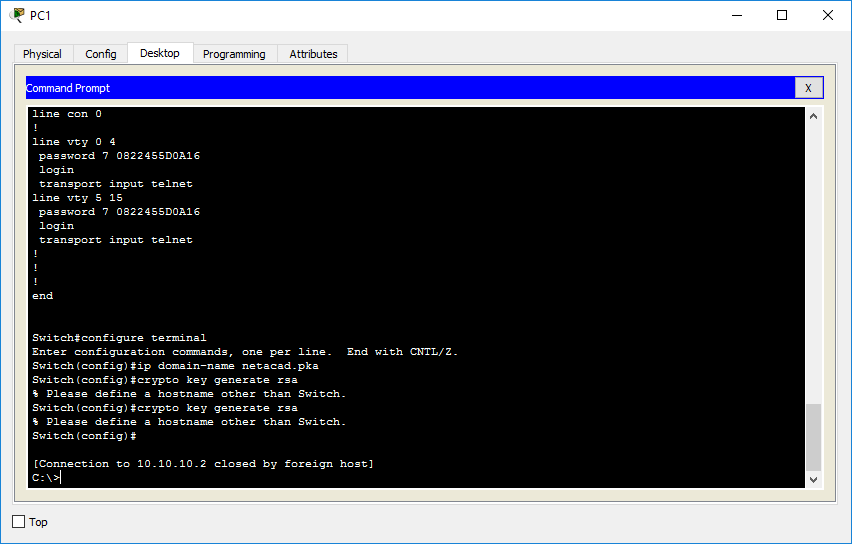
The name for the keys will be. Generate csr via cisco asa cli commands 1. Crypto key generate rsa cryptokeygeneratersa page2 cisco ios security command reference. For these key to work you should have a hostname domain name configured on the asa as well unless you configure a dedicated rsa keys. So basically configure a hostname domain name and generate the rsa key pair.

The name for the keys. Commands a to c cisco ios xe release 3se catalyst 3850 switches. The asas do have vpns configured. The following example specifies the redundancy keyword. The ecdsa algorithm is a part of the elliptic curve cryptography ecc and uses an equation of an elliptic curve to generate a public key whereas the rsa algorithm uses the product of two primes plus a smaller number to generate the public key.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site value, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title generate crypto key cisco asa by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.





