Crypto random generator java images are ready. Crypto random generator java are a topic that is being searched for and liked by netizens now. You can Find and Download the Crypto random generator java files here. Download all free photos and vectors.
If you’re looking for crypto random generator java images information related to the crypto random generator java keyword, you have visit the right site. Our site always provides you with suggestions for seeing the highest quality video and image content, please kindly surf and find more informative video content and graphics that match your interests.
Crypto Random Generator Java. Most random number generators are hardware dependent or require specialized hardware. Cryptographic hash is a hash function that takes random size input and yields a fixed size output. To generate keys using the keygenerator class follow the steps given below. A cryptographically strong random number minimally complies with the statistical random number generator tests specified in fips 140 2 security requirements for cryptographic modules section 4 9 1 additionally securerandom must produce non deterministic output.
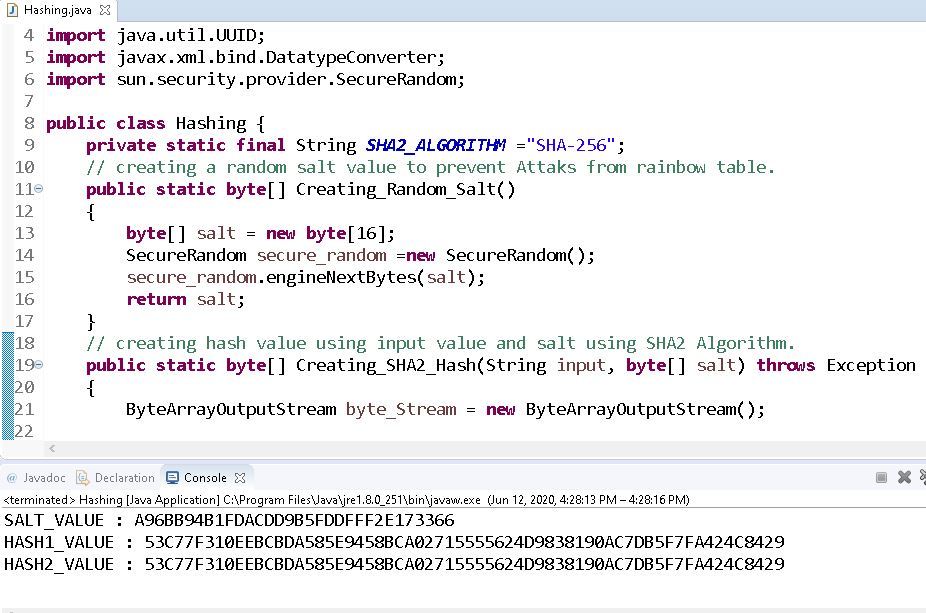 Cryptographic Hash Function In Java Geeksforgeeks From geeksforgeeks.org
Cryptographic Hash Function In Java Geeksforgeeks From geeksforgeeks.org
The keygenerator class provides getinstance method which accepts a string variable representing the required key generating algorithm and returns a keygenerator. Java by principle is hardware independent and so uses pseudorandom number. This class provides a cryptographically strong random number generator rng. Java provides keygenerator class this class is used to generate secret keys and objects of this class are reusable. Most random number generators are hardware dependent or require specialized hardware. That s why i ll show you an.
To generate keys using the keygenerator class follow the steps given below.
Pseudo random functions which are not secure for cryptography usually use an internal state at the start the state is initialized by an initial seed when the next random number is generated it is calculated from the internal state using some computation or formula then the internal state of the pseudo random function is changed using some computation or formula. It is easy to calculate but challenging to retrieve original data. To generate keys using the keygenerator class follow the steps given below. It is strong and difficult to duplicate the same hash with unique inputs and is a one way function so revert is not possible. Random generates a random double number and uses random class internally to do that. A cryptographically strong random number minimally complies with the statistical random number generator tests specified in fips 140 2 security requirements for cryptographic modules section 4 9 1 additionally securerandom must produce non deterministic output.
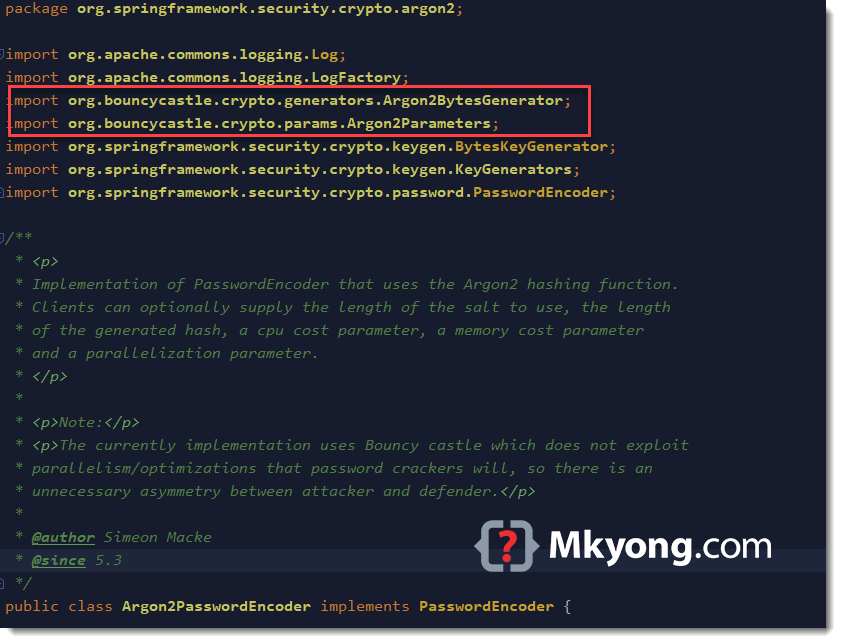 Source: laptrinhx.com
Source: laptrinhx.com
Random numbers are crucial to cryptography. A cryptographically strong random number minimally complies with the statistical random number generator tests specified in fips 140 2 security requirements for cryptographic modules section 4 9 1 additionally securerandom must produce non deterministic output. The keygenerator class provides getinstance method which accepts a string variable representing the required key generating algorithm and returns a keygenerator. Random numbers are crucial to cryptography. This class provides a cryptographically strong random number generator rng.
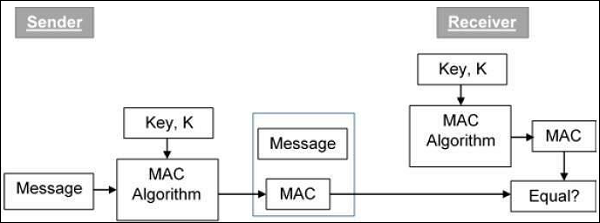
 Source: medium.com
Source: medium.com
Java provides keygenerator class this class is used to generate secret keys and objects of this class are reusable. Cryptographic hash is a hash function that takes random size input and yields a fixed size output. Random class has a lot of methods but nextint is the most popular. It is easy to calculate but challenging to retrieve original data. Random generates a random double number and uses random class internally to do that.
 Source: tutorialspoint.com
Source: tutorialspoint.com
It is strong and difficult to duplicate the same hash with unique inputs and is a one way function so revert is not possible. That s why i ll show you an. It is strong and difficult to duplicate the same hash with unique inputs and is a one way function so revert is not possible. Most random number generators are hardware dependent or require specialized hardware. Create a keygenerator object.
 Source: geeksforgeeks.org
Source: geeksforgeeks.org
Let s take a look at code examples. It is strong and difficult to duplicate the same hash with unique inputs and is a one way function so revert is not possible. The java keygenerator class javax crypto keygenerator is used to generate symmetric encryption keys a symmetric encryption key is a key that is used for both encryption and decryption of data by a symmetric encryption algorithm. Cryptographic hash is a hash function that takes random size input and yields a fixed size output. If you need a cryptographically secure random generator use java.
 Source: stackoverflow.com
Source: stackoverflow.com
That s why i ll show you an. A cryptographically strong random number minimally complies with the statistical random number generator tests specified in fips 140 2 security requirements for cryptographic modules section 4 9 1 additionally securerandom must produce non deterministic output. In this java keygenerator tutorial i will show you how to generate symmetric encryption keys. Random class has a lot of methods but nextint is the most popular. It is strong and difficult to duplicate the same hash with unique inputs and is a one way function so revert is not possible.
 Source: mobilefish.com
Source: mobilefish.com
In the developer s world it is a common task to generate a random number in a situation like where we need to send an otp to a user for authentication or need to generate secure salt which will be used in cryptography etc. In the developer s world it is a common task to generate a random number in a situation like where we need to send an otp to a user for authentication or need to generate secure salt which will be used in cryptography etc. Cryptographic hash is a hash function that takes random size input and yields a fixed size output. The java keygenerator class javax crypto keygenerator is used to generate symmetric encryption keys a symmetric encryption key is a key that is used for both encryption and decryption of data by a symmetric encryption algorithm. A cryptographically strong random number minimally complies with the statistical random number generator tests specified in fips 140 2 security requirements for cryptographic modules section 4 9 1 additionally securerandom must produce non deterministic output.
 Source: stackoverflow.com
Source: stackoverflow.com
Pseudo random functions which are not secure for cryptography usually use an internal state at the start the state is initialized by an initial seed when the next random number is generated it is calculated from the internal state using some computation or formula then the internal state of the pseudo random function is changed using some computation or formula. They are used to create cryptographic keys and to encrypt or sign data. Random numbers are crucial to cryptography. This class provides a cryptographically strong random number generator rng. Java has had historic difficulty generating random numbers.
 Source: docs.oracle.com
Source: docs.oracle.com
A cryptographically strong random number minimally complies with the statistical random number generator tests specified in fips 140 2 security requirements for cryptographic modules section 4 9 1 additionally securerandom must produce non deterministic output. That s why i ll show you an. Java by principle is hardware independent and so uses pseudorandom number. Most random number generators are hardware dependent or require specialized hardware. In this java random number generator article we will learn how to generate random in java and generate random numbers in a specific range.
 Source: billthelizard.blogspot.com
Source: billthelizard.blogspot.com
This class provides a cryptographically strong random number generator rng. In the developer s world it is a common task to generate a random number in a situation like where we need to send an otp to a user for authentication or need to generate secure salt which will be used in cryptography etc. Random generates a random double number and uses random class internally to do that. A cryptographically strong random number minimally complies with the statistical random number generator tests specified in fips 140 2 security requirements for cryptographic modules section 4 9 1 additionally securerandom must produce non deterministic output. It is strong and difficult to duplicate the same hash with unique inputs and is a one way function so revert is not possible.
 Source: mkyong.com
Source: mkyong.com
This class provides a cryptographically strong random number generator rng. In this java random number generator article we will learn how to generate random in java and generate random numbers in a specific range. To generate keys using the keygenerator class follow the steps given below. They are used to create cryptographic keys and to encrypt or sign data. In the developer s world it is a common task to generate a random number in a situation like where we need to send an otp to a user for authentication or need to generate secure salt which will be used in cryptography etc.
 Source: journaldev.com
Source: journaldev.com
Pseudo random functions which are not secure for cryptography usually use an internal state at the start the state is initialized by an initial seed when the next random number is generated it is calculated from the internal state using some computation or formula then the internal state of the pseudo random function is changed using some computation or formula. It is strong and difficult to duplicate the same hash with unique inputs and is a one way function so revert is not possible. Cryptographic hash is a hash function that takes random size input and yields a fixed size output. Random class has a lot of methods but nextint is the most popular. Random generates a random double number and uses random class internally to do that.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site convienient, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title crypto random generator java by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.





